You are here
Technology
3 pernicious myths of responsible AI
Responsible AI (RAI) is needed now more than ever. It is the key to driving everything from trust and adoption, to managing LLM hallucinations and eliminating toxic generative AI content. With effective RAI, companies can innovate faster, transform more parts of the business, comply with future AI regulation, and prevent fines, reputational damage, and competitive stagnation.
Unfortunately, confusion reigns as to what RAI actually is, what it delivers, and how to achieve it, with potentially catastrophic effects. Done poorly, RAI initiatives stymie innovation, creating hurdles that add delays and costs without actually improving safety. Well-meaning, but misguided, myths abound regarding the very definition and purpose of RAI. Organizations must shatter these myths if we are to turn RAI into a force for AI-driven value creation, instead of a costly, ineffectual time sink.
Understanding Microsoft’s Trusted Signing service
How do we ensure that the code we’re installing is, at the very least, the code that a vendor shipped? The generally accepted solution is code signing, adding a digital signature to binaries that can be used to ensure authorship. At the same time, the signature includes a hash that can be used to show that the code you’ve received hasn’t been altered after it’s been signed.
Code signing is increasingly important as part of ensuring software bills of materials and reducing the risks associated with malware hijacking legitimate binaries. Signing is necessary if you’re planning on using services like the Microsoft Store or the Windows Package Manager to distribute your applications, allowing the repository to verify software sources.
Replace Calendar with LocalDate in Java programs
Developers often need to perform programming operations such as retrieving the current date, manipulating dates, and formatting dates in their applications. While Java's traditional java.util.Calendar class had its day, the newer LocalDate class does more with significantly fewer lines of code. This article introduces you to LocalDate and the java.time API for using dates, times, and durations in your programs.
Note: Introduced in Java 8, java.time standardizes many elements of the popular Joda-Time library. Concepts introduced here can be applied to either library but the JDK standard is generally recommended.
Svelte 5 moves to release candidate stage
Svelte 5, a planned update to the reactive UI framework, has reached the release candidate phase. No breaking changes are anticipated between now and the stable release.
The release candidate was announced on April 30. It features a rewrite of Svelte to be faster, easier to use, and more robust. Runes, a signal-powered reactivity API, is a highlight of this release. Runes promises to unlock universal, fine-grained reactivity, the Svelte team said.
Google lays off Flutter, Dart staffers – reports
Along with releasing Python specialists, Google also has laid off Flutter and Dart teams according to various reports.
Google did not respond this morning to InfoWorld's inquiry about Flutter and Dart layoffs. But comments were circulating online about staff reductions at Google. Flutter is an open source framework for building multi-platform applications from a single codebase. Dart, a language leveraged by Flutter, was once positioned as a rival to JavaScript.
Java 17 is most-used LTS version of Java – report
Java 17, a Long Term Support (LTS) version of the Java language released in September 2021, has become the most-used Java LTS version, according to New Relic’s 2024 State of the Java Ecosystem report, published April 30. Java 21, an LTS version released in 2023, also is seeing higher adoption.
More than 35% of applications are using Java 17 in production this year, compared to 9.1% in 2023, observability provider New Relic reported. Java 17, also known as JDK 17, has overtaken Java 11, from September 2018, as the most-used LTS version. The adoption rate of Java 21, though, was 287% higher in the first six months after its release than that of Java 17, New Relic said.
MongoDB aims to jumpstart AI app development with MAAP
MongoDB has introduced the MongoDB AI Applications Program, or MAAP, to help enterprises jumpstart their development of generative AI applications.
MAAP, according to the company, will offer enterprises strategic advice, professional services, and an integrated end-to-end technology stack from MongoDB and its partners.
These partners include consultancies, foundation model (FM) providers, cloud infrastructure providers, and generative AI framework and model hosting providers including Anthropic, Anyscale, Amazon Web Services (AWS), Cohere, Credal.ai, Fireworks.ai, Google Cloud, gravity9, LangChain, LlamaIndex, Microsoft Azure, Nomic, PeerIslands, Pureinsights, and Together AI.
6 Rust programming mistakes to watch out for
Rust offers programmers a way to write memory-safe software without garbage collection, running at machine-native speed. It's also a complex language to master, with a fairly steep initial learning curve. Here are five gotchas, snags, and traps to watch for when you're getting your footing with Rust—and for more seasoned Rust developers, too.
Rust gotchas: 6 things you need to know about writing Rust code- You can't 'toggle off' the borrow checker
- Don't use '_' for variables you want to bind
- Closures don't have the same lifetime rules as functions
- Destructors don't always run when a borrow expires
- Beware of unsafe things and unbounded lifetimes
- .unwrap() surrenders error-handling control
Ownership, borrowing, and lifetimes are baked into Rust. They're an integral part of how the language maintains memory safety without garbage collection.
How to use JavaScript statements in your programs
JavaScript statements control the overall flow of JavaScript programs. Statements are used to declare variables and manage iterative processes, and they can also be used to declare classes and functions.
Unlike properties, methods, and events, which are inseparable from the object that owns them, statements work independently. That means you can use a statement in any context, whether you're programming a client-side or server-side application. As a language, JavaScript supports relatively few statements—just enough to construct functional applications.
About the authorsAn earlier version of this article was written by Gordon McComb and published on JavaWorld. Matthew Tyson updated the article with newer syntax and code examples in May 2024.
SN 972: Passkeys: A Shattered Dream? - IoT Default Passwords, Passkeys
- GCHQ: No more default passwords for consumer IoT devices!
- What happened with Chrome and 3rd-party cookies?
- Race conditions and multi-threading
- GM "accidentally" enrolled millions into "OnStar Smart Driver +" program
- Steve recommends Ryk Brown's "Frontiers Saga"
- SpinRite update
- Passkeys: A Shattered Dream?
Show Notes - https://www.grc.com/sn/SN-972-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to this show at https://twit.tv/shows/security-now.
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Sponsors:
OpenSilver 2.2 shines on LightSwitch
Userware has released OpenSilver 2.2, an update to the company’s open-source replacement for Microsoft’s Silverlight rich internet application framework. This release lets legacy Visual Studio LightSwitch applications run on modern browsers via a compatibility pack.
OpenSilver 2.2 and the LightSwitch Compatibility Pack were announced April 30. Developers can download OpenSilver 2.2 and sign up for a trial of LightSwitch Compatibility Pack. With the Userware updates, Lightswitch applications can be ported without rewriting them.
Amazon Q for developers is generally available
Amazon Web Services (AWS) on Tuesday said that it was making its generative AI-powered coding assistant Amazon Q Developer generally available.
Introduced as the evolution of Amazon CodeWhisperer at AWS re:Invent in November, Amazon Q will compete with rival offerings such as GitHub Copilot, Gemini Code Assist, and IBM’s Watsonx Code Assistant, AWS said.
How TigerGraph CoPilot enables graph-augmented AI
Data has the potential to provide transformative business insights across various industries, yet harnessing that data presents significant challenges. Many businesses struggle with data overload, with vast amounts of data that are siloed and underutilized. How can organizations deal with large and growing volumes of data without sacrificing performance and operational efficiency? Another challenge is extracting insights from complex data. Traditionally, this work has required significant technical expertise, restricting access to specialized data scientists and analysts.
Recent AI breakthroughs in natural language processing are democratizing data access, enabling a wider range of users to query and interpret complex data sets. This broadened access helps organizations make informed decisions swiftly, capitalizing on the capability of AI copilots to process and analyze large-scale data in real time. AI copilots can also curb the high costs associated with managing large data sets by automating complex data processes and empowering less technical staff to undertake sophisticated data analysis, thus optimizing overall resource allocation.
Man Who Mass-Extorted Psychotherapy Patients Gets Six Years
A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an online psychotherapy clinic, leaking tens of thousands of patient therapy records, and attempting to extort the clinic and patients.
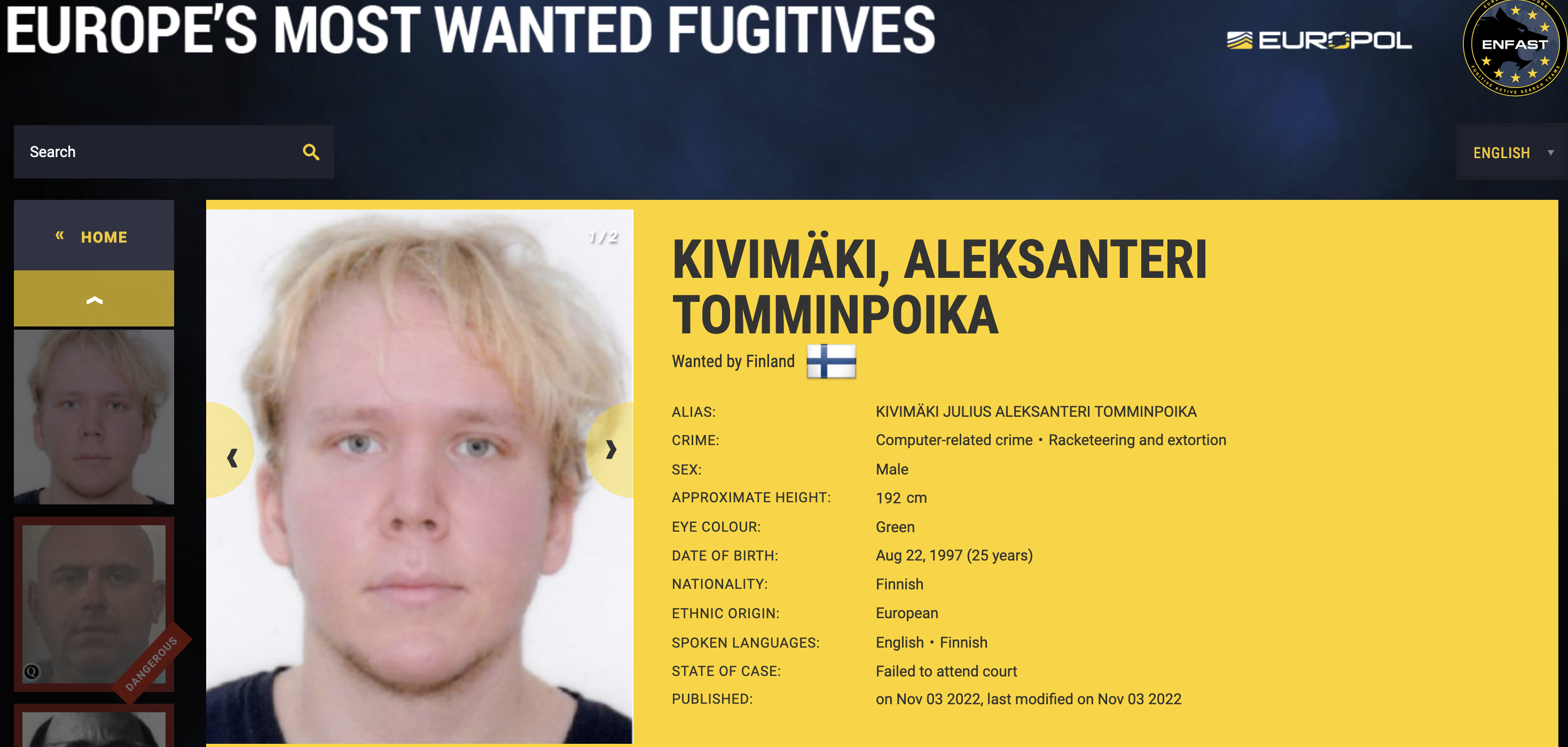
On October 21, 2020, the Vastaamo Psychotherapy Center in Finland became the target of blackmail when a tormentor identified as “ransom_man” demanded payment of 40 bitcoins (~450,000 euros at the time) in return for a promise not to publish highly sensitive therapy session notes Vastaamo had exposed online.
Ransom_man announced on the dark web that he would start publishing 100 patient profiles every 24 hours. When Vastaamo declined to pay, ransom_man shifted to extorting individual patients. According to Finnish police, some 22,000 victims reported extortion attempts targeting them personally, targeted emails that threatened to publish their therapy notes online unless paid a 500 euro ransom.
Finnish prosecutors quickly zeroed in on a suspect: Julius “Zeekill” Kivimäki, a notorious criminal hacker convicted of committing tens of thousands of cybercrimes before he became an adult. After being charged with the attack in October 2022, Kivimäki fled the country. He was arrested four months later in France, hiding out under an assumed name and passport.
Antii Kurittu is a former criminal investigator who worked on an investigation involving Kivimäki’s use of the Zbot botnet, among other activities Kivimäki engaged in as a member of the hacker group Hack the Planet (HTP).
Kurittu said the prosecution had demanded at least seven years in jail, and that the sentence handed down was six years and three months. Kurittu said prosecutors agreed to knock a few months off of Kivimäki’s sentence because he agreed to pay compensation to his victims, and that Kivimäki will remain in prison during any appeal process.
“I think the sentencing was as expected, knowing the Finnish judicial system,” Kurittu told KrebsOnSecurity. “As Kivimäki has not been sentenced to a non-suspended prison sentence during the last five years, he will be treated as a first-timer, his previous convictions notwithstanding.”
But because juvenile convictions in Finland don’t count towards determining whether somebody is a first-time offender, Kivimäki will end up serving approximately half of his sentence.
“This seems like a short sentence when taking into account the gravity of his actions and the life-altering consequences to thousands of people, but it’s almost the maximum the law allows for,” Kurittu said.
Kivimäki initially gained notoriety as a self-professed member of the Lizard Squad, a mainly low-skilled hacker group that specialized in DDoS attacks. But American and Finnish investigators say Kivimäki’s involvement in cybercrime dates back to at least 2008, when he was introduced to a founding member of what would soon become HTP.
Finnish police said Kivimäki also used the nicknames “Ryan”, “RyanC” and “Ryan Cleary” (Ryan Cleary was actually a member of a rival hacker group — LulzSec — who was sentenced to prison for hacking).
Kivimäki and other HTP members were involved in mass-compromising web servers using known vulnerabilities, and by 2012 Kivimäki’s alias Ryan Cleary was selling access to those servers in the form of a DDoS-for-hire service. Kivimäki was 15 years old at the time.
In 2013, investigators going through devices seized from Kivimäki found computer code that had been used to crack more than 60,000 web servers using a previously unknown vulnerability in Adobe’s ColdFusion software. KrebsOnSecurity detailed the work of HTP in September 2013, after the group compromised servers inside data brokers LexisNexis, Kroll, and Dun & Bradstreet.
The group used the same ColdFusion flaws to break into the National White Collar Crime Center (NWC3), a non-profit that provides research and investigative support to the U.S. Federal Bureau of Investigation (FBI).
As KrebsOnSecurity reported at the time, this small ColdFusion botnet of data broker servers was being controlled by the same cybercriminals who’d assumed control over SSNDOB, which operated one of the underground’s most reliable services for obtaining Social Security Number, dates of birth and credit file information on U.S. residents.
Kivimäki was responsible for making an August 2014 bomb threat against former Sony Online Entertainment President John Smedley that grounded an American Airlines plane. Kivimäki also was involved in calling in multiple fake bomb threats and “swatting” incidents — reporting fake hostage situations at an address to prompt a heavily armed police response to that location.
Ville Tapio, the former CEO of Vastaamo, was fired and also prosecuted following the breach. Ransom_man bragged about Vastaamo’s sloppy security, noting the company had used the laughably weak username and password “root/root” to protect sensitive patient records.
Investigators later found Vastaamo had originally been hacked in 2018 and again in 2019, but that Tapio never told anyone about the intrusions until ransom_man began his extortion spree. In April 2023, a Finnish court handed down a three-month sentence for Tapio, but that sentence was suspended because he had no previous criminal record.
Teradata adds support for Apache Iceberg, Delta Lake tables
Teradata is adding support for two open table formats, Apache Iceberg and Linux Foundation’s Delta Lake, to its multi-cloud analytics platform VantageCloud Lake and its AI and machine learning engine Unlimited AI.
Typically, open table formats are architected to generate performance for data lakes using cloud-based object storage. The performance is achieved by creating a layer of abstraction atop a data lake via the use of columnar storage and metadata management that allows enterprises to manage and update data more efficiently.
How cloud cost visibility impacts business and employment
In its latest The State of Cloud Cost in 2024 report, CloudZero illuminates the serious implications of cloud cost management and its effect on business stability and job security. The conclusions are interesting.
CloudZero’s survey, which drew insights from 1,000 finance and engineering professionals, underscored a crucial element in cloud cost management: the pivotal role of engineering teams. These are not just the “nerds” who operate the technology but key players who can significantly influence cost outcomes.
According to the survey, 81% of respondents indicated that cloud costs were effectively managed and predictable when engineers managed them. This shows a positive relationship between engineering ownership and better cloud cost management. This shift in perception has significant business implications for effective cloud cost management.
Google lays off Python team – reports
Several online news outlets report that Google laid off its entire Python language team. However, Google denied that the layoffs were company-wide when asked about the fate of the team.
Reports of the Python team’s dismissal have shown up in Reddit, Hacker News, and social.coop. “Google’s Python team was a small team, most of which were also on the Python steering council or core Python developers,” one commenter said in Hacker News. “These people had decades of experience in Python. Their knowledge and community connections [are] irreplaceable.”
GitHub previews GitHub Copilot Workspace
GitHub is offering a technical preview of GitHub Copilot Workspace, which provides a developer environment based on the GitHub Copilot AI-powered programming assistant.
The GitHub Copilot Workspace preview was introduced April 29. Described as a Copilot-native development environment for everyday tasks, GitHub Copilot Workspace allows developers “to brainstorm, plan, build, test, and run code in natural language,” GitHub said. GitHub Copilot Chat, the natural language assistant, was introduced in November.
FCC Fines Major U.S. Wireless Carriers for Selling Customer Location Data
The U.S. Federal Communications Commission (FCC) today levied fines totaling nearly $200 million against the four major carriers — including AT&T, Sprint, T-Mobile and Verizon — for illegally sharing access to customers’ location information without consent.
![]()
The fines mark the culmination of a more than four-year investigation into the actions of the major carriers. In February 2020, the FCC put all four wireless providers on notice that their practices of sharing access to customer location data were likely violating the law.
The FCC said it found the carriers each sold access to its customers’ location information to ‘aggregators,’ who then resold access to the information to third-party location-based service providers.
“In doing so, each carrier attempted to offload its obligations to obtain customer consent onto downstream recipients of location information, which in many instances meant that no valid customer consent was obtained,” an FCC statement on the action reads. “This initial failure was compounded when, after becoming aware that their safeguards were ineffective, the carriers continued to sell access to location information without taking reasonable measures to protect it from unauthorized access.”
The FCC’s findings against AT&T, for example, show that AT&T sold customer location data directly or indirectly to at least 88 third-party entities. The FCC found Verizon sold access to customer location data (indirectly or directly) to 67 third-party entities. Location data for Sprint customers found its way to 86 third-party entities, and to 75 third-parties in the case of T-Mobile customers.
The commission said it took action in response to a May 2018 story broken by The New York Times, which exposed how a company called Securus Technologies had been selling location data on customers of virtually any major mobile provider to law enforcement officials.
That same month, KrebsOnSecurity broke the news that LocationSmart — a data aggregation firm working with the major wireless carriers — had a free, unsecured demo of its service online that anyone could abuse to find the near-exact location of virtually any mobile phone in North America.
The carriers promised to “wind down” location data sharing agreements with third-party companies. But in 2019, reporting at Vice.com showed that little had changed, detailing how reporters were able to locate a test phone after paying $300 to a bounty hunter who simply bought the data through a little-known third-party service.
The FCC fined Sprint and T-Mobile $12 million and $80 million respectively. AT&T was fined more than $57 million, while Verizon received a $47 million penalty. Still, these fines represent a tiny fraction of each carrier’s annual revenues. For example, $47 million is less than one percent of Verizon’s total wireless service revenue in 2023, which was nearly $77 billion.
The fine amounts vary because they were calculated based in part on the number of days that the carriers continued sharing customer location data after being notified that doing so was illegal (the agency also considered the number of active third-party location data sharing agreements). The FCC notes that AT&T and Verizon each took more than 320 days from the publication of the Times story to wind down their data sharing agreements; T-Mobile took 275 days; Sprint kept sharing customer location data for 386 days.