You are here
Technology
TWiT 1072: The Devil's Advocate - Jailbreaking Fighter Jets, Social Media Addiction, and Self-Driving Snafus
What do jailbreaking fighter jets, lost Amazon vans, and swapping your phone's smart features for a handful of mud have in common? TWiT dives into the wild, occasionally absurd future of tech, where yesterday's sci-fi is tomorrow's supply-chain headache.
- Mark Zuckerberg and his Ray-Ban entourage have their day in court
- Instagram Boss Says 16 Hours of Daily Use Is Not Addiction
- Meta Begins $65 Million Election Push To Advance AI Agenda - Slashdot
- Australia's Social Media Ban Is Isolating Kids With Disabilities—Just Like Critics Warned
- Google I/O 2026 set for May 19-20
- Pixel 10A hands-on: More like a slightly better Pixel 9A than a slightly worse Pixel 10
- Google announces Gemini 3.1 Pro, says it's better at complex problem-solving
- Tucson Daily Brief
- Leaked Email Suggests Ring Plans to Expand 'Search Party' Surveillance Beyond Dogs
- A $10K+ bounty is waiting for anyone who can unplug Ring doorbells from Amazon’s cloud
- Amazon delivery van accidentally gets stuck in the sea in Britain
- Tesla 'Robotaxi' adds 5 more crashes in Austin in a month – 4x worse than humans
- Government Docs Reveal New Details About Tesla and Waymo Robotaxis' Human Babysitters
- The Supreme Court's Tariff Ruling Won't Bring Car Prices Back to Earth
- A flood of cheap used EVs is coming
- Signal guide for everyday folks
- PayPal discloses data breach that exposed user info for 6 months
- Federal ban on TP-Link routers shelved, but Texas fights on
- You probably can't trust your password manager if it's compromised
- Mississippi health system shuts down clinics statewide after ransomware attack
- Fake Job Recruiters Hid Malware In Developer Coding Challenges
- F-35 Software Could Be Jailbreaked Like an IPhone: Dutch Defense Minister - Slashdot
- In a blind test, audiophiles couldn't tell the difference between audio signals sent through copper wire, a banana, or wet mud — 'The mud should sound perfectly awful, but it doesn't,' notes the experiment creator | Tom's Hardware
- Lab-Grown Meat Exists (But Nobody Wants To Eat It)
- CERN rebuilt the original browser from 1989
Host: Leo Laporte
Guests: Sam Abuelsamid, Fr. Robert Ballecer, SJ, and Nicholas De Leon
Download or subscribe to This Week in Tech at https://twit.tv/shows/this-week-in-tech
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
‘Starkiller’ Phishing Service Proxies Real Login Pages, MFA
Most phishing websites are little more than static copies of login pages for popular online destinations, and they are often quickly taken down by anti-abuse activists and security firms. But a stealthy new phishing-as-a-service offering lets customers sidestep both of these pitfalls: It uses cleverly disguised links to load the target brand’s real website, and then acts as a relay between the target and the legitimate site — forwarding the victim’s username, password and multi-factor authentication (MFA) code to the legitimate site and returning its responses.
There are countless phishing kits that would-be scammers can use to get started, but successfully wielding them requires some modicum of skill in configuring servers, domain names, certificates, proxy services, and other repetitive tech drudgery. Enter Starkiller, a new phishing service that dynamically loads a live copy of the target login page and records everything the user types, proxying the data to the legitimate site and back to the victim.
According to an analysis of Starkiller by the security firm Abnormal AI, the service lets customers select a brand to impersonate (e.g., Apple, Facebook, Google, Microsoft et. al.) and generates a deceptive URL that visually mimics the legitimate domain while routing traffic through the attacker’s infrastructure.
For example, a phishing link targeting Microsoft customers appears as “login.microsoft.com@[malicious/shortened URL here].” The “@” sign in the link trick is an oldie but goodie, because everything before the “@” in a URL is considered username data, and the real landing page is what comes after the “@” sign. Here’s what it looks like in the target’s browser:

Image: Abnormal AI. The actual malicious landing page is blurred out in this picture, but we can see it ends in .ru. The service also offers the ability to insert links from different URL-shortening services.
Once Starkiller customers select the URL to be phished, the service spins up a Docker container running a headless Chrome browser instance that loads the real login page, Abnormal found.
“The container then acts as a man-in-the-middle reverse proxy, forwarding the end user’s inputs to the legitimate site and returning the site’s responses,” Abnormal researchers Callie Baron and Piotr Wojtyla wrote in a blog post on Thursday. “Every keystroke, form submission, and session token passes through attacker-controlled infrastructure and is logged along the way.”
Starkiller in effect offers cybercriminals real-time session monitoring, allowing them to live-stream the target’s screen as they interact with the phishing page, the researchers said.
“The platform also includes keylogger capture for every keystroke, cookie and session token theft for direct account takeover, geo-tracking of targets, and automated Telegram alerts when new credentials come in,” they wrote. “Campaign analytics round out the operator experience with visit counts, conversion rates, and performance graphs—the same kind of metrics dashboard a legitimate SaaS [software-as-a-service] platform would offer.”
Abnormal said the service also deftly intercepts and relays the victim’s MFA credentials, since the recipient who clicks the link is actually authenticating with the real site through a proxy, and any authentication tokens submitted are then forwarded to the legitimate service in real time.
“The attacker captures the resulting session cookies and tokens, giving them authenticated access to the account,” the researchers wrote. “When attackers relay the entire authentication flow in real time, MFA protections can be effectively neutralized despite functioning exactly as designed.”
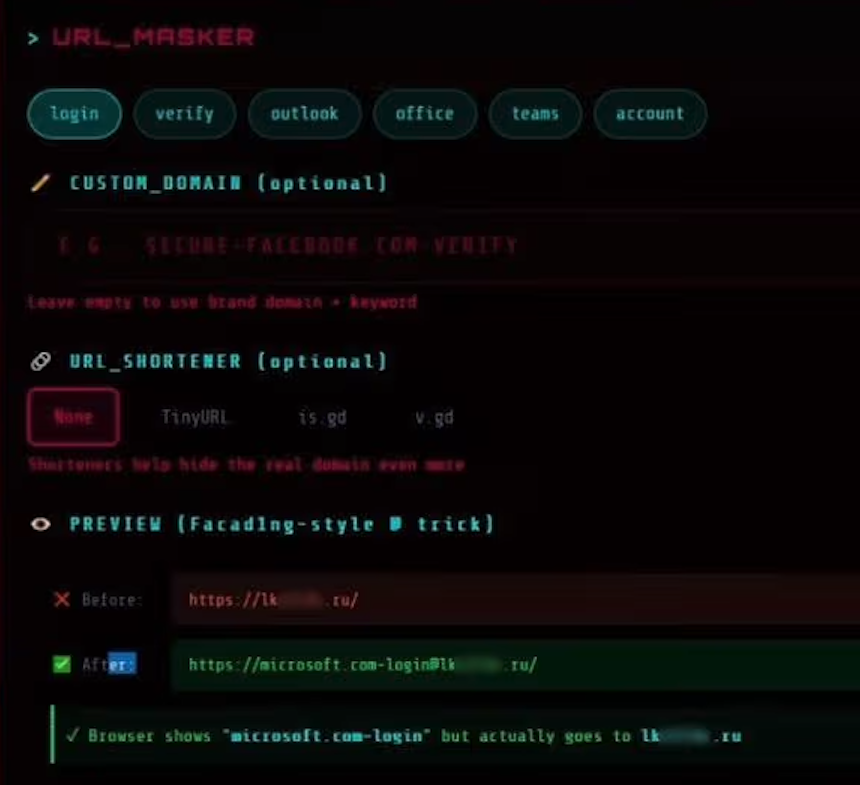
The “URL Masker” feature of the Starkiller phishing service features options for configuring the malicious link. Image: Abnormal.
Starkiller is just one of several cybercrime services offered by a threat group calling itself Jinkusu, which maintains an active user forum where customers can discuss techniques, request features and troubleshoot deployments. One a-la-carte feature will harvest email addresses and contact information from compromised sessions, and advises the data can be used to build target lists for follow-on phishing campaigns.
This service strikes me as a remarkable evolution in phishing, and its apparent success is likely to be copied by other enterprising cybercriminals (assuming the service performs as well as it claims). After all, phishing users this way avoids the upfront costs and constant hassles associated with juggling multiple phishing domains, and it throws a wrench in traditional phishing detection methods like domain blocklisting and static page analysis.
It also massively lowers the barrier to entry for novice cybercriminals, Abnormal researchers observed.
“Starkiller represents a significant escalation in phishing infrastructure, reflecting a broader trend toward commoditized, enterprise-style cybercrime tooling,” their report concludes. “Combined with URL masking, session hijacking, and MFA bypass, it gives low-skill cybercriminals access to attack capabilities that were previously out of reach.”
SN 1065: Attestation - Code Signing Gets Tough
How secure are your Chrome extensions and certificate signings really? This episode pulls back the curtain on a massive spyware discovery and exposes the convoluted hoops developers must jump through to prove their identity in 2026.
- Websites can place high demands upon limited CPU resources.
- Microsoft appears to back away from its security commitment.
- What's Windows 11 26H1 and where do I get it.
- Chrome 145 brings Device Bound Session Credentials.
- More countries are moving to ban underage social media use.
- The return of Roskomnadzor.
- Discord to require proof of adulthood for adult content.
- Might you still be using WinRAR 7.12 -- I was.
- Paragon's Graphite can definitely spy on all instant messaging.
- 30 malicious Chrome Extensions.
- 287 Chrome extensions from spying on 37.4 million users.
- The first malicious Outlook add-in steals 4000 user's credentials.
- Some AI "vibe" coding thoughts.
- What I just went through to obtain a new code signing certificate
Show Notes - https://www.grc.com/sn/SN-1065-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to Security Now at https://twit.tv/shows/security-now.
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
TWiT 1071: Image Pickles - Are Social Platforms Addictive or Just Too Good?
Is social media addictive by design or just irresistible entertainment? The panel tackles the lawsuit that's dragging tech giants onto the witness stand and how surveillance tech is quietly expanding while lawmakers and users scramble to catch up.
- Jury told that Meta, Google 'engineered addiction' at landmark US trial
- Instagram Chief Says Social Media Is Not 'Clinically Addictive' in Landmark Trial
- Section 230 turns 30 as it faces its biggest tests yet
- Meta apparently thinks we're too distracted to care about facial recognition and Ray-Bans
- Amazon Ring's Super Bowl ad sparks backlash amid fears of mass surveillance
- Ring cancels its partnership with Flock Safety after surveillance backlash
- TikTok is tracking you, even if you don't use the app.
- Discord backtracks on controversial age verification rollout...kind of
- Discord/Twitch/Snapchat age verification bypass
- The DJI Romo robovac had security so poor that this man remotely accessed thousands of them
- HP's laptop subscriptions are a great deal — for HP
- FTC Ratchets Up Microsoft Probe, Queries Rivals on Cloud, AI
- T-Mobile announces its network is now full of AI by rolling out real-time translation
- Apple's latest attempt to launch the new Siri runs into snags
- SpaceX Prioritizes Lunar 'Self-Growing City' Over Mars Project, Musk Says
- Elon Musk declares victory with Medicaid data release
- Waymo Is Getting DoorDashers to Close Doors on Self Driving Cars
- Backblaze Drive Stats for 2025
- $1.8 million MST3K Kickstarter brings in (almost) everyone from the old show
- OpenAI Is Nuking Its 4o Model. China's ChatGPT Fans Aren't OK
- Hideki Sato, designer of all Sega's consoles, has died
- Byte magazine artist Robert Tinney, who illustrated the birth of PCs, dies at 78
- Launching The Rural Guaranteed Minimum Income Initiative
Host: Leo Laporte
Guests: Wesley Faulkner, Stacey Higginbotham, and Thomas Germain
Download or subscribe to This Week in Tech at https://twit.tv/shows/this-week-in-tech
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
The Linux Link Tech Show Episode 1127
Kimwolf Botnet Swamps Anonymity Network I2P
For the past week, the massive “Internet of Things” (IoT) botnet known as Kimwolf has been disrupting The Invisible Internet Project (I2P), a decentralized, encrypted communications network designed to anonymize and secure online communications. I2P users started reporting disruptions in the network around the same time the Kimwolf botmasters began relying on it to evade takedown attempts against the botnet’s control servers.
Kimwolf is a botnet that surfaced in late 2025 and quickly infected millions of systems, turning poorly secured IoT devices like TV streaming boxes, digital picture frames and routers into relays for malicious traffic and abnormally large distributed denial-of-service (DDoS) attacks.
I2P is a decentralized, privacy-focused network that allows people to communicate and share information anonymously.
“It works by routing data through multiple encrypted layers across volunteer-operated nodes, hiding both the sender’s and receiver’s locations,” the I2P website explains. “The result is a secure, censorship-resistant network designed for private websites, messaging, and data sharing.”
On February 3, I2P users began complaining on the organization’s GitHub page about tens of thousands of routers suddenly overwhelming the network, preventing existing users from communicating with legitimate nodes. Users reported a rapidly increasing number of new routers joining the network that were unable to transmit data, and that the mass influx of new systems had overwhelmed the network to the point where users could no longer connect.
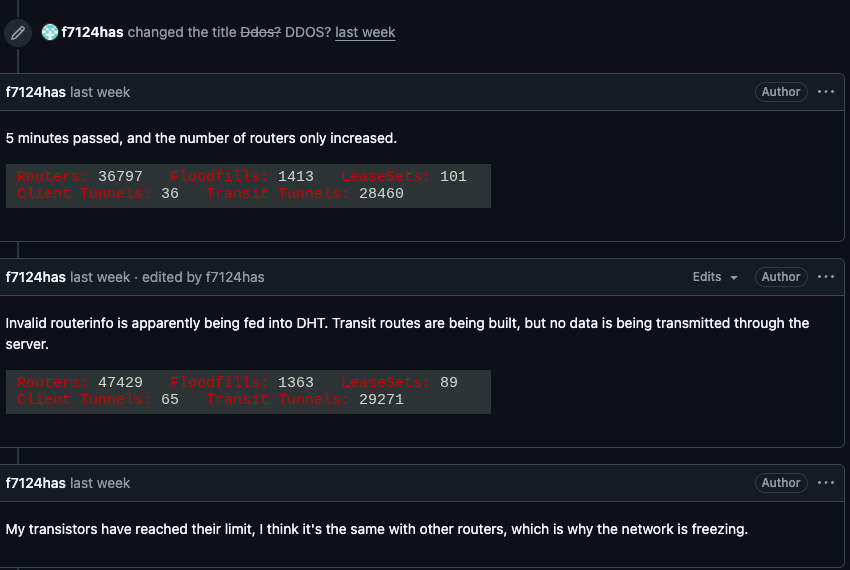
I2P users complaining about service disruptions from a rapidly increasing number of routers suddenly swamping the network.
When one I2P user asked whether the network was under attack, another user replied, “Looks like it. My physical router freezes when the number of connections exceeds 60,000.”
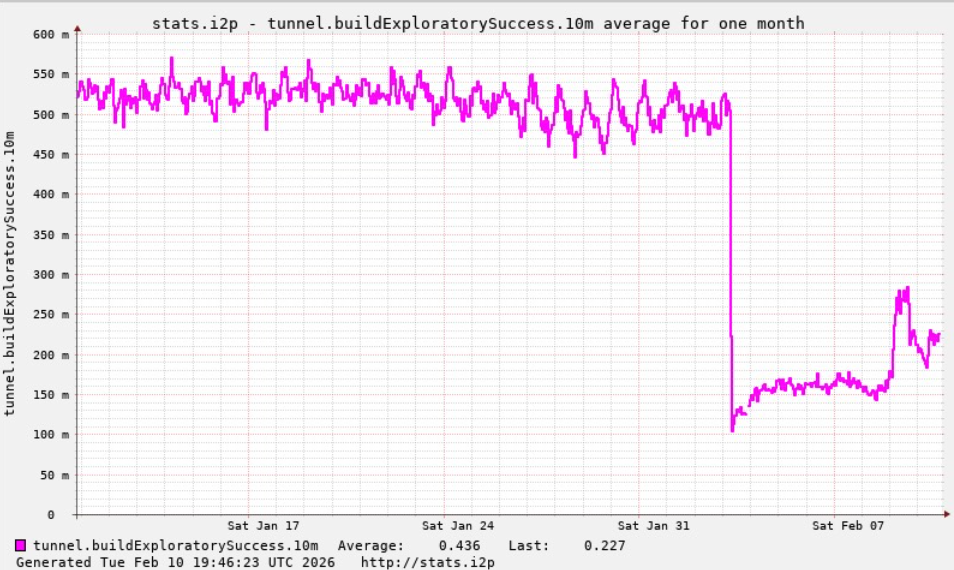
A graph shared by I2P developers showing a marked drop in successful connections on the I2P network around the time the Kimwolf botnet started trying to use the network for fallback communications.
The same day that I2P users began noticing the outages, the individuals in control of Kimwolf posted to their Discord channel that they had accidentally disrupted I2P after attempting to join 700,000 Kimwolf-infected bots as nodes on the network.
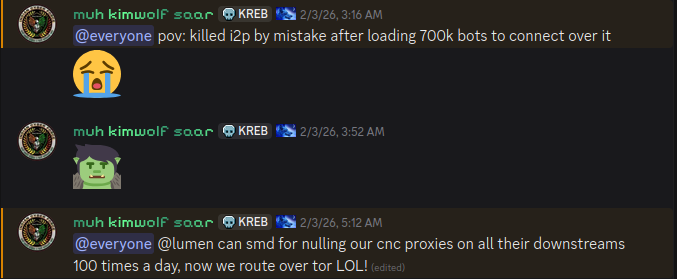
The Kimwolf botmaster openly discusses what they are doing with the botnet in a Discord channel with my name on it.
Although Kimwolf is known as a potent weapon for launching DDoS attacks, the outages caused this week by some portion of the botnet attempting to join I2P are what’s known as a “Sybil attack,” a threat in peer-to-peer networks where a single entity can disrupt the system by creating, controlling, and operating a large number of fake, pseudonymous identities.
Indeed, the number of Kimwolf-infected routers that tried to join I2P this past week was many times the network’s normal size. I2P’s Wikipedia page says the network consists of roughly 55,000 computers distributed throughout the world, with each participant acting as both a router (to relay traffic) and a client.
However, Lance James, founder of the New York City based cybersecurity consultancy Unit 221B and the original founder of I2P, told KrebsOnSecurity the entire I2P network now consists of between 15,000 and 20,000 devices on any given day.
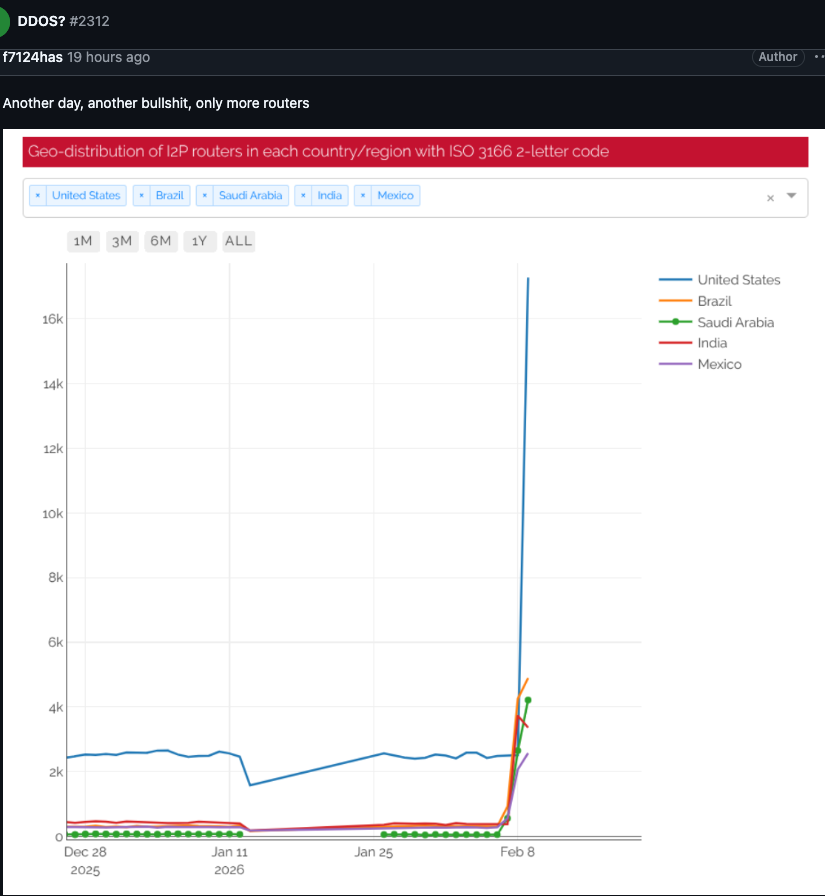
An I2P user posted this graph on Feb. 10, showing tens of thousands of routers — mostly from the United States — suddenly attempting to join the network.
Benjamin Brundage is founder of Synthient, a startup that tracks proxy services and was the first to document Kimwolf’s unique spreading techniques. Brundage said the Kimwolf operator(s) have been trying to build a command and control network that can’t easily be taken down by security companies and network operators that are working together to combat the spread of the botnet.
Brundage said the people in control of Kimwolf have been experimenting with using I2P and a similar anonymity network — Tor — as a backup command and control network, although there have been no reports of widespread disruptions in the Tor network recently.
“I don’t think their goal is to take I2P down,” he said. “It’s more they’re looking for an alternative to keep the botnet stable in the face of takedown attempts.”
The Kimwolf botnet created challenges for Cloudflare late last year when it began instructing millions of infected devices to use Cloudflare’s domain name system (DNS) settings, causing control domains associated with Kimwolf to repeatedly usurp Amazon, Apple, Google and Microsoft in Cloudflare’s public ranking of the most frequently requested websites.
James said the I2P network is still operating at about half of its normal capacity, and that a new release is rolling out which should bring some stability improvements over the next week for users.
Meanwhile, Brundage said the good news is Kimwolf’s overlords appear to have quite recently alienated some of their more competent developers and operators, leading to a rookie mistake this past week that caused the botnet’s overall numbers to drop by more than 600,000 infected systems.
“It seems like they’re just testing stuff, like running experiments in production,” he said. “But the botnet’s numbers are dropping significantly now, and they don’t seem to know what they’re doing.”
SN 1064: Least Privilege - Cybercrime Goes Pro
From EU fines that never get paid to cyber warfare grounding missiles mid-battle, this week's episode uncovers the untold stories and real-world consequences shaping today's digital defenses.
- How is the EU's GDPR fine collection going.
- Western democracies are getting serious about offensive cybercrime.
- The powerful cyber component of the Midnight Hammer operation.
- Signs of psychological dependence upon OpenAI's GPT-4o chatbot.
- CISA orders government agencies to unplug end-of-support devices.
- How to keep Windows from annoying us after an upgrade.
- What is OpenClaw, how safe is it to use, what does it mean.
- Another listener uses AI to completely code an app.
- Coinbase suffers another insider breach. What can be done
Show Notes - https://www.grc.com/sn/SN-1064-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to Security Now at https://twit.tv/shows/security-now.
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
Patch Tuesday, February 2026 Edition
Microsoft today released updates to fix more than 50 security holes in its Windows operating systems and other software, including patches for a whopping six “zero-day” vulnerabilities that attackers are already exploiting in the wild.

Zero-day #1 this month is CVE-2026-21510, a security feature bypass vulnerability in Windows Shell wherein a single click on a malicious link can quietly bypass Windows protections and run attacker-controlled content without warning or consent dialogs. CVE-2026-21510 affects all currently supported versions of Windows.
The zero-day flaw CVE-2026-21513 is a security bypass bug targeting MSHTML, the proprietary engine of the default Web browser in Windows. CVE-2026-21514 is a related security feature bypass in Microsoft Word.
The zero-day CVE-2026-21533 allows local attackers to elevate their user privileges to “SYSTEM” level access in Windows Remote Desktop Services. CVE-2026-21519 is a zero-day elevation of privilege flaw in the Desktop Window Manager (DWM), a key component of Windows that organizes windows on a user’s screen. Microsoft fixed a different zero-day in DWM just last month.
The sixth zero-day is CVE-2026-21525, a potentially disruptive denial-of-service vulnerability in the Windows Remote Access Connection Manager, the service responsible for maintaining VPN connections to corporate networks.
Chris Goettl at Ivanti reminds us Microsoft has issued several out-of-band security updates since January’s Patch Tuesday. On January 17, Microsoft pushed a fix that resolved a credential prompt failure when attempting remote desktop or remote application connections. On January 26, Microsoft patched a zero-day security feature bypass vulnerability (CVE-2026-21509) in Microsoft Office.
Kev Breen at Immersive notes that this month’s Patch Tuesday includes several fixes for remote code execution vulnerabilities affecting GitHub Copilot and multiple integrated development environments (IDEs), including VS Code, Visual Studio, and JetBrains products. The relevant CVEs are CVE-2026-21516, CVE-2026-21523, and CVE-2026-21256.
Breen said the AI vulnerabilities Microsoft patched this month stem from a command injection flaw that can be triggered through prompt injection, or tricking the AI agent into doing something it shouldn’t — like executing malicious code or commands.
“Developers are high-value targets for threat actors, as they often have access to sensitive data such as API keys and secrets that function as keys to critical infrastructure, including privileged AWS or Azure API keys,” Breen said. “When organizations enable developers and automation pipelines to use LLMs and agentic AI, a malicious prompt can have significant impact. This does not mean organizations should stop using AI. It does mean developers should understand the risks, teams should clearly identify which systems and workflows have access to AI agents, and least-privilege principles should be applied to limit the blast radius if developer secrets are compromised.”
The SANS Internet Storm Center has a clickable breakdown of each individual fix this month from Microsoft, indexed by severity and CVSS score. Enterprise Windows admins involved in testing patches before rolling them out should keep an eye on askwoody.com, which often has the skinny on wonky updates. Please don’t neglect to back up your data if it has been a while since you’ve done that, and feel free to sound off in the comments if you experience problems installing any of these fixes.
TWiT 1070: A Yacht for Your Yacht - Super Bowl LX Gets a Surge of AI Ads!
Will Elon Musk really launch a million data centers into orbit, and why is McDonald's so worried about you using "McNuggets" as your password? This week's tech roundtable takes on wild new frontiers and everyday security headaches with insight and a bit of irreverence.
- More schools are banning phones so students can focus. Ohio's results show it's not that simple
- After Australia, Which Countries Could Be Next to Ban Social Media for Children
- EU says TikTok must disable 'addictive' features like infinite scroll, fix its recommendation engine
- Anthropic and OpenAI release dueling AI models on the same day in an escalating rivalry
- Sam Altman says Anthropic's Super Bowl spot is 'dishonest' about ChatGPT ads, but he agrees it's funny
- Anthropic's Claude Opus 4.6 uncovers 500 zero-day flaws in open-source code
- Alphabet reports Q4 2025 revenue of $113.8 billion
- Amazon's blowout $200 billion AI spending plan stuns Wall Street
- A New Gilded Age: Big Tech goes on a $600 billion AI spending splurge
- Hidden Cameras in Chinese Hotels Are Livestreaming Guests To Thousands of Telegram Subscribers
- AI-generated ads hit the Super Bowl
- SpaceX acquires xAI, plans to launch a massive satellite constellation to power it
- Russia suspected of intercepting EU satellites
- Notepad++ hijacked by state-sponsored actors
- New York Wants to Ctrl+Alt+Delete Your 3D Printer
- Western Digital Plots a Path To 140 TB Hard Drives Using Vertical Lasers and 14-Platter Designs
- A Crisis comes to Wordle: Reusing old words
- The Wayback Machine debuts a new plug-in designed to fix the internet's broken links problem
- Project Hail Mary is getting its own LEGO set
- Dave Farber
Host: Leo Laporte
Guests: Larry Magid, Mike Elgan, and Louis Maresca
Download or subscribe to This Week in Tech at https://twit.tv/shows/this-week-in-tech
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
The Linux Link Tech Show Episode 1126
SN 1063: Mongo's Too Easy - AI Bug Bounties Gone Wild
When a popular antivirus and even Notepad++ turn into infection vectors after supply chain breaches, it's clear no software is safe from attack—or from its own update system. Steve and Leo unpack the risks hiding right inside your next auto-update.
- An anti-virus system infects its own users.
- Apple's next iOS release "fuzzes" cellular locations.
- cURL discontinues bug bounties under bogus AI flood.
- AI discovers and fixes 15 CVE-worthy 0-days in OpenSSL.
- Ireland did NOT already pass their spying legislation.
- AI irreversibly deletes all project files. Says it's sorry.
- Windows has a serious global clipboard security problem.
- ISPs have the ability to monetize their subscriber's identities.
- MongoDB has lowered the hacking skill level bar to the floor
Show Notes - https://www.grc.com/sn/SN-1063-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to Security Now at https://twit.tv/shows/security-now.
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
Please Don’t Feed the Scattered Lapsus ShinyHunters
A prolific data ransom gang that calls itself Scattered Lapsus ShinyHunters (SLSH) has a distinctive playbook when it seeks to extort payment from victim firms: Harassing, threatening and even swatting executives and their families, all while notifying journalists and regulators about the extent of the intrusion. Some victims reportedly are paying — perhaps as much to contain the stolen data as to stop the escalating personal attacks. But a top SLSH expert warns that engaging at all beyond a “We’re not paying” response only encourages further harassment, noting that the group’s fractious and unreliable history means the only winning move is not to pay.

Image: Shutterstock.com, @Mungujakisa
Unlike traditional, highly regimented Russia-based ransomware affiliate groups, SLSH is an unruly and somewhat fluid English-language extortion gang that appears uninterested in building a reputation of consistent behavior whereby victims might have some measure of confidence that the criminals will keep their word if paid.
That’s according to Allison Nixon, director of research at the New York City based security consultancy Unit 221B. Nixon has been closely tracking the criminal group and individual members as they bounce between various Telegram channels used to extort and harass victims, and she said SLSH differs from traditional data ransom groups in other important ways that argue against trusting them to do anything they say they’ll do — such as destroying stolen data.
Like SLSH, many traditional Russian ransomware groups have employed high-pressure tactics to force payment in exchange for a decryption key and/or a promise to delete stolen data, such as publishing a dark web shaming blog with samples of stolen data next to a countdown clock, or notifying journalists and board members of the victim company. But Nixon said the extortion from SLSH quickly escalates way beyond that — to threats of physical violence against executives and their families, DDoS attacks on the victim’s website, and repeated email-flooding campaigns.
SLSH is known for breaking into companies by phishing employees over the phone, and using the purloined access to steal sensitive internal data. In a January 30 blog post, Google’s security forensics firm Mandiant said SLSH’s most recent extortion attacks stem from incidents spanning early to mid-January 2026, when SLSH members pretended to be IT staff and called employees at targeted victim organizations claiming that the company was updating MFA settings.
“The threat actor directed the employees to victim-branded credential harvesting sites to capture their SSO credentials and MFA codes, and then registered their own device for MFA,” the blog post explained.
Victims often first learn of the breach when their brand name is uttered on whatever ephemeral new public Telegram group chat SLSH is using to threaten, extort and harass their prey. According to Nixon, the coordinated harassment on the SLSH Telegram channels is part of a well-orchestrated strategy to overwhelm the victim organization by manufacturing humiliation that pushes them over the threshold to pay.
Nixon said multiple executives at targeted organizations have been subject to “swatting” attacks, wherein SLSH communicated a phony bomb threat or hostage situation at the target’s address in the hopes of eliciting a heavily armed police response at their home or place of work.
“A big part of what they’re doing to victims is the psychological aspect of it, like harassing executives’ kids and threatening the board of the company,” Nixon told KrebsOnSecurity. “And while these victims are getting extortion demands, they’re simultaneously getting outreach from media outlets saying, ‘Hey, do you have any comments on the bad things we’re going to write about you.”
In a blog post today, Unit 221B argues that no one should negotiate with SLSH because the group has demonstrated a willingness to extort victims based on promises that it has no intention to keep. Nixon points out that all of SLSH’s known members hail from The Com, shorthand for a constellation of cybercrime-focused Discord and Telegram communities which serve as a kind of distributed social network that facilitates instant collaboration.
Nixon said Com-based extortion groups tend to instigate feuds and drama between group members, leading to lying, betrayals, credibility destroying behavior, backstabbing, and sabotaging each other.
“With this type of ongoing dysfunction, often compounding by substance abuse, these threat actors often aren’t able to act with the core goal in mind of completing a successful, strategic ransom operation,” Nixon wrote. “They continually lose control with outbursts that put their strategy and operational security at risk, which severely limits their ability to build a professional, scalable, and sophisticated criminal organization network for continued successful ransoms – unlike other, more tenured and professional criminal organizations focused on ransomware alone.”
Intrusions from established ransomware groups typically center around encryption/decryption malware that mostly stays on the affected machine. In contrast, Nixon said, ransom from a Com group is often structured the same as violent sextortion schemes against minors, wherein members of The Com will steal damaging information, threaten to release it, and “promise” to delete it if the victim complies without any guarantee or technical proof point that they will keep their word. She writes:
A key component of SLSH’s efforts to convince victims to pay, Nixon said, involves manipulating the media into hyping the threat posed by this group. This approach also borrows a page from the playbook of sextortion attacks, she said, which encourages predators to keep targets continuously engaged and worrying about the consequences of non-compliance.
“On days where SLSH had no substantial criminal ‘win’ to announce, they focused on announcing death threats and harassment to keep law enforcement, journalists, and cybercrime industry professionals focused on this group,” she said.

An excerpt from a sextortion tutorial from a Com-based Telegram channel. Image: Unit 221B.
Nixon knows a thing or two about being threatened by SLSH: For the past several months, the group’s Telegram channels have been replete with threats of physical violence against her, against Yours Truly, and against other security researchers. These threats, she said, are just another way the group seeks to generate media attention and achieve a veneer of credibility, but they are useful as indicators of compromise because SLSH members tend to name drop and malign security researchers even in their communications with victims.
“Watch for the following behaviors in their communications to you or their public statements,” Unit 221B’s advisory reads. “Repeated abusive mentions of Allison Nixon (or “A.N”), Unit 221B, or cybersecurity journalists—especially Brian Krebs—or any other cybersecurity employee, or cybersecurity company. Any threats to kill, or commit terrorism, or violence against internal employees, cybersecurity employees, investigators, and journalists.”
Unit 221B says that while the pressure campaign during an extortion attempt may be traumatizing to employees, executives, and their family members, entering into drawn-out negotiations with SLSH incentivizes the group to increase the level of harm and risk, which could include the physical safety of employees and their families.
“The breached data will never go back to the way it was, but we can assure you that the harassment will end,” Nixon said. “So, your decision to pay should be a separate issue from the harassment. We believe that when you separate these issues, you will objectively see that the best course of action to protect your interests, in both the short and long term, is to refuse payment.”
TWiT 1069: In My Head I Have 3 Buckets - Moltbook Becomes a Surreal AI Agent Social Network
What happens when AI bots get their own social network, Silicon Valley execs cozy up to power, and Apple takes a cut from creators? This week's panel calls out the bold, bizarre, and often problematic ways tech's biggest players are reshaping everything from AI assistants to your everyday privacy.
- There's a social network for AI agents, and it's getting weird
- Moltbook is the most interesting place on the internet right now
- Exposed Moltbook Database Let Anyone Take Control of Any AI Agent on the Site
- Pentagon clashes with Anthropic over military AI use, sources say
- Salesforce signs $5.6B deal to inject agentic AI into the US Army
- Angry Norfolk residents lose lawsuit to stop Flock license plate scanners
- SpaceX wants to put 1 million solar-powered data centers into orbit
- Elon Musk reportedly wants a June SpaceX IPO to align with his birthday, the planets
- Tesla hits a grim milestone: its second straight year of decline
- Tesla says production-ready Optimus robot is coming soon
- Microsoft reports strong cloud earnings in Q2 as gaming declines
- What We Learned From Meta, Microsoft and Tesla
- Apple tells Patreon to move creators to in-app purchase for subscriptions by November
- Apple CEO Tim Cook 'heartbroken' after repeated ICE killings in Minneapolis
- A rival smart glasses company is suing Meta over its Ray-Ban products
- TikTok, YouTube, and Meta are headed to court for a landmark trial over social media addiction
- The 'Social Media Addiction' Narrative May Be More Harmful Than Social Media Itself
- TikTok users freak out over app's 'immigration status' collection — here's what it means
- A Waymo hit a child near an elementary school in Santa Monica
- Autonomous cars, drones cheerfully obey prompt injection by road sign
- Samsung's TriFold phone will cost $2,899 in the US
- Groundhogs are bad at predicting weather, but they're valuable animal engineers\
- Satellites encased in wood are in the works
- Belkin reminds users that its Wemo smart home products are shutting down this week
Host: Leo Laporte
Guests: Gary Rivlin, Devindra Hardawar, and Victoria Song
Download or subscribe to This Week in Tech at https://twit.tv/shows/this-week-in-tech
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors:
The Linux Link Tech Show Episode 1125
SN 1062: AI-Generated Malware - Ireland Legalizes Spyware
Can AI really write malware better than hackers ever could? This episode exposes the first real-world case of advanced, fully AI-generated malware and why it signals a seismic shift in cybersecurity risk.
- CISA's uncertain future remains quite worrisome.
- Worrisome is Ireland's new "lawful" interception law.
- The EU's Digital Rights organization pushes back.
- Microsoft acknowledges it turns over user encryption keys.
- Alex Neihaus on AI enterprise usage dangers.
- Gavin confesses he put a database on the Internet.
- Worries about a massive podcast rewinding backlog.
- What does the emergence of AI-generated malware portend?
Show Note - https://www.grc.com/sn/SN-1062-Notes.pdf
Hosts: Steve Gibson and Leo Laporte
Download or subscribe to Security Now at https://twit.tv/shows/security-now.
You can submit a question to Security Now at the GRC Feedback Page.
For 16kbps versions, transcripts, and notes (including fixes), visit Steve's site: grc.com, also the home of the best disk maintenance and recovery utility ever written Spinrite 6.
Join Club TWiT for Ad-Free Podcasts!
Support what you love and get ad-free audio and video feeds, a members-only Discord, and exclusive content. Join today: https://twit.tv/clubtwit
Sponsors: